Black Basta Ransomware (RaaS) syndicate has claimed nearly 50 victims in the United States, Canada, Australia, New Zealand, and the United Kingdom within two months of its debut. In a short amount of time, it has become a significant threat.
Black Basta Ransomware has targeted various industries, According to research by Cybereason, including manufacturing, construction, transportation, telecommunications, pharmaceuticals, cosmetics, plumbing & heating, vehicle dealers, lingerie manufacturers, and more.
According to evidence, the ransomware strain was still under development as recently as February 2022. It wasn’t until it was advertised on the dark web forums that it bought and monetized access to the corporate network in exchange for a cut of the profits that it began to be used in attacks starting in April.
Black Basta is known to use the tried-and-true strategy of double extortion, similar to previous ransomware operations, to steal important information from the targets and threaten to disseminate the stolen data unless a digital payment is made.
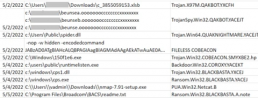
Figure 1. A timeline of the files detected on the infected machine
The breaches involving the threat, a newcomer in the already crowded ransomware arena, have used QBot (also known as Qakbot) as a conduit to retain persistence on the compromised systems and gather credentials before going lateral across the network and spreading the file-encrypting malware.
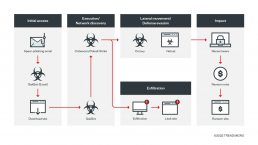
Figure 2. The infection chain from the point of entry to the Black Basta Ransomware payload
A Linux variant created by Black Basta’s perpetrators to attack VMware ESXi virtual machines (VMs) running on enterprise systems also puts it on par with organizations like LockBit, Hive, and Cheerscrypt.
According to security researcher Ido Cohen, Elbit Systems of America, a provider of defence, aerospace, and security technologies, was recently added to the victims of the cybercriminal organization.
According to reports, the Conti organization, which shut down its operations in response to heightened law enforcement scrutiny and a significant leak that revealed its tools and techniques after siding with Russia in the country’s conflict with Ukraine, is made up of members of Black Basta.
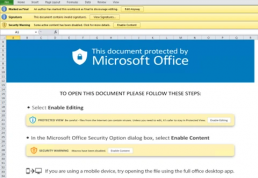
Figure 3. Instructions in the Excel file used by QakBot to lure a potential victim into enabling Excel 4.0 macros
The Ukrainian computer expert who leaked the data under the alias Danylo told CNN in March 2022: “I cannot shoot anything, but I can fight with a keyboard and mouse.” He did it as a sort of digital retaliation.
Since then, the Conti team has denied any affiliation with Black Basta. The criminal operation came to an end last week when the rest of its publicly visible infrastructure was shut down, including two Tor servers used to leak data and communicate with victims.
The organization underwent organizational changes that caused it to fragment into smaller subgroups with various goals and business models, including data theft and operating as independent affiliates. Meanwhile, the group continued to maintain the semblance of an active operation targeting the Costa Rican government.
The Conti Group is believed to have compromised over 40 businesses worldwide as part of a “lightning-fast” hacking spree that ran from November 17 to December 20, 2021, according to a detailed report from Group-IB outlining its operations since it was first noticed in February 2020.
The intrusions, code-named “ARMattack” by the Singapore-based company, targeted American organizations most frequently (37 percent), then those in Germany (3 percent), Switzerland (2 percent), the United Arab Emirates (2 percent), the Netherlands, Spain, France, the Czech Republic, Sweden, Denmark, and India (1 percent each).
The top five industries historically targeted by Conti were manufacturing (14%), real estate (11.1%), logistics (8.2%), professional services (7.1%), and trade (5.5%). In addition, the operators singled out companies in the United States (58.4%), Canada (7%), the U.K. (6.6%), Germany (5.8%), France (3.9%), and Italy in particular (3.1 percent ).
Group-IB’s Ivan Pisarev stated that Conti’s increasing activity and data breaches “indicate that ransomware is no more a game between amateur malware creators, but rather an illicit RaaS enterprise that employs hundreds of cybercriminals worldwide with a variety of skills.”
“Conti is a well-known figure in this field who founded an “IT firm” with the express purpose of extorting significant quantities of money. It seems obvious that the group will carry on with its business, either independently or with the aid of its “subsidiary” initiatives.”
Image sources: Trend Micro (https://www.trendmicro.com/en_us/research/22/f/black-basta-ransomware-operators-expand-their-attack-arsenal-wit.html)
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.