RhynoGUARD MDR
Delivering Robust SOC Operations as a Service
Our team of Rhyno Cybersecurity experts conducts round-the-clock monitoring of your entire infrastructure, covering network, endpoint, email, cloud, and IoT. This enables you to make well-informed decisions for halting ongoing attacks and fine-tuning your defenses to proactively thwart future threats.
The Benefits of RhynoGUARD Managed Detection and Response (MDR)
Prioritizing Prevention
Implementing top-tier strategies for defense enhancement and attack prevention
Streamlined Approach
Accessing around-the-clock service by our elite experts
Enhanced Security Measures
Implementing advanced threat prevention driven by AI-driven analytics
A Comprehensive Solution
Handling prevention, monitoring, detection, investigation, and remediation of attacks
Prioritized Alert Management
Efficient cyber threat response
24/7 Threat Hunting
Monitoring and analysis of data
Security Optimization
Secure, operational, accessible
Tools and integrations
For complete 360 visibility
Alert Management
Get alerts where you need them
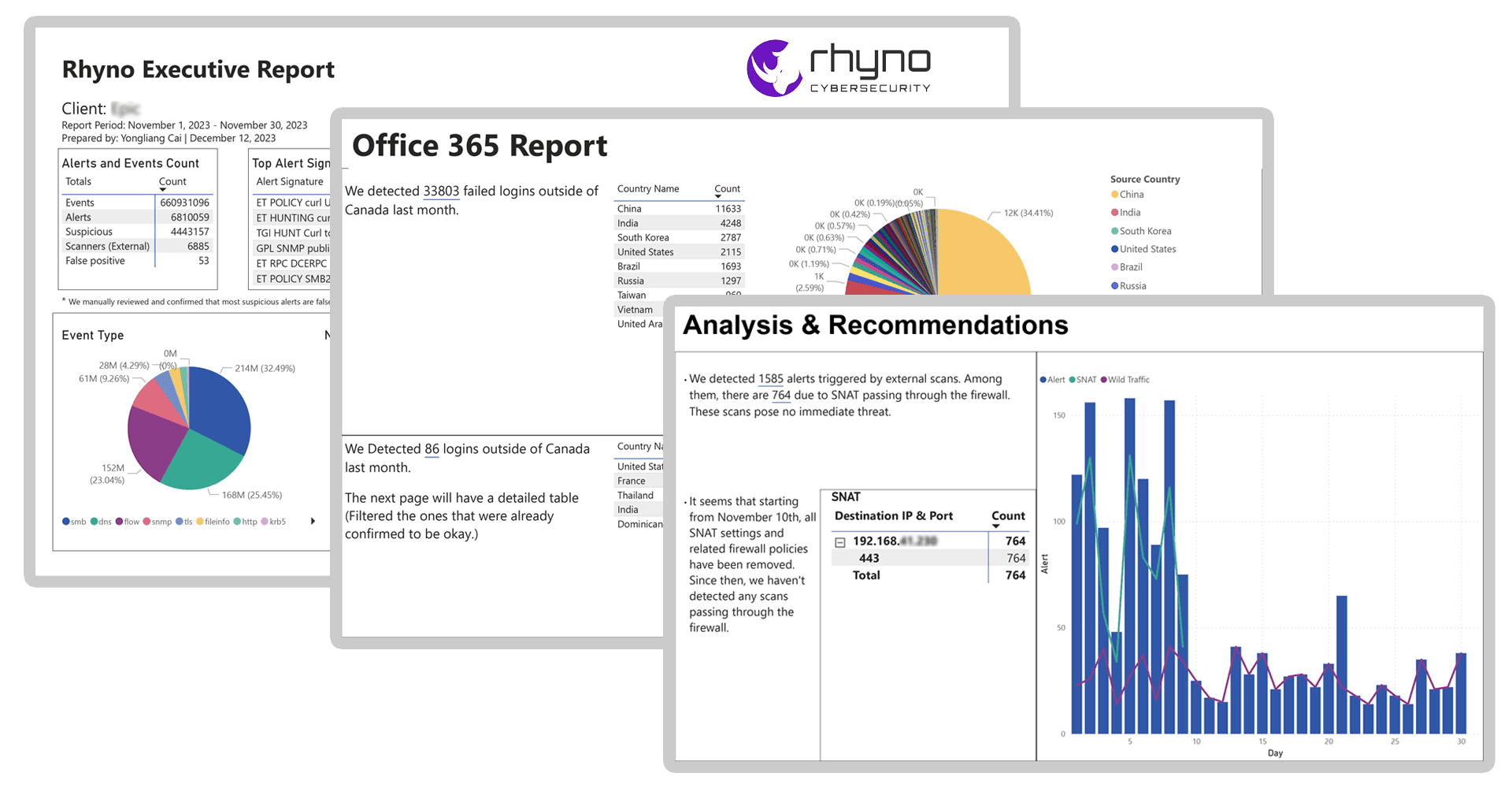
Customized Reporting
Technical and recommendations
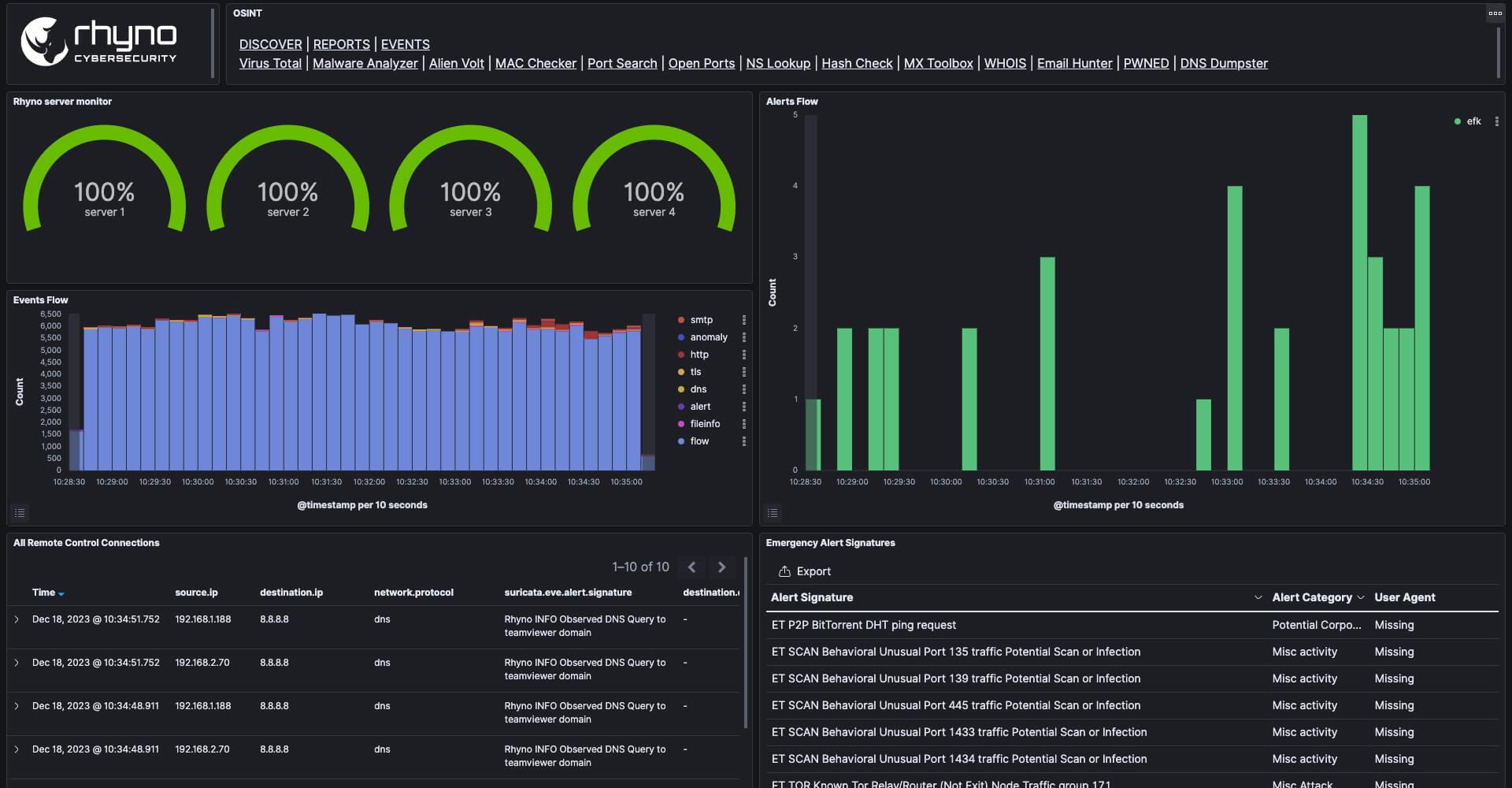
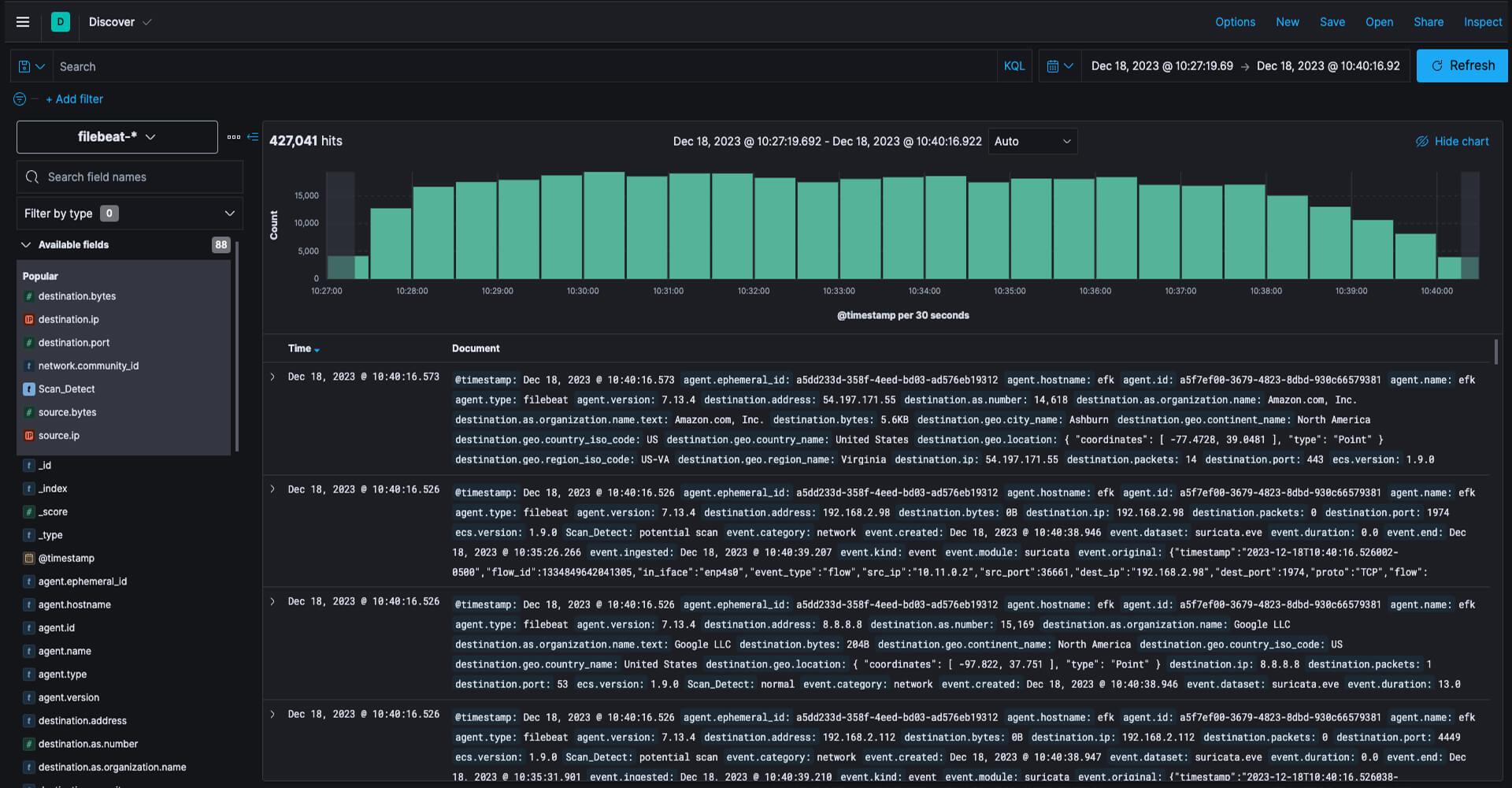
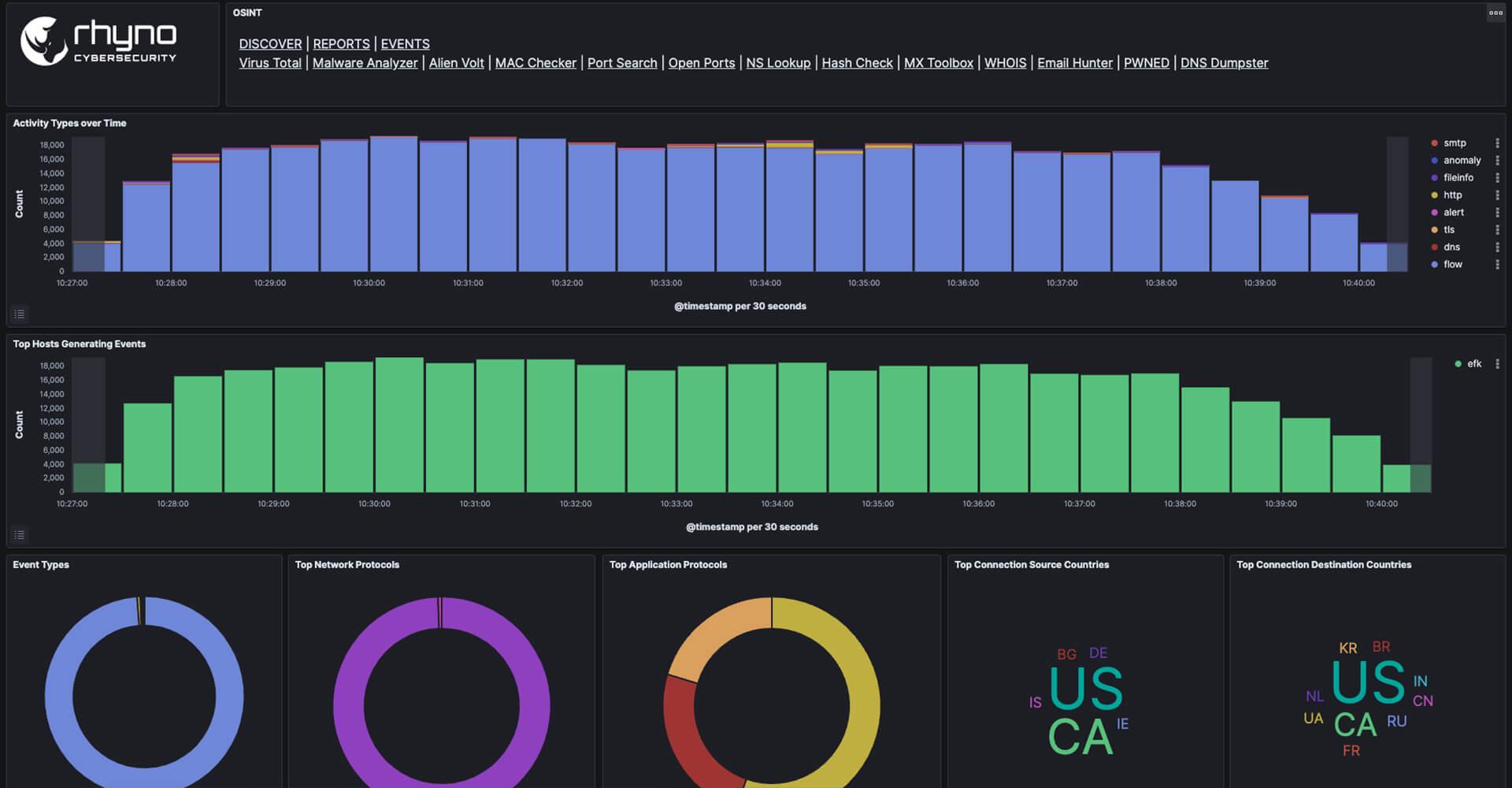
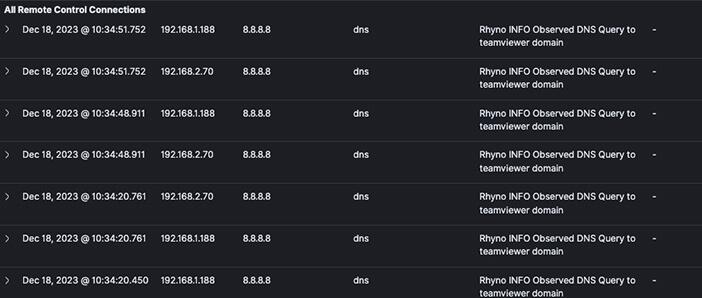
Remote Connections
Robust system to identify and triage remote connections effectively. By monitoring network traffic, we can spot DNS queries to known remote service domains.
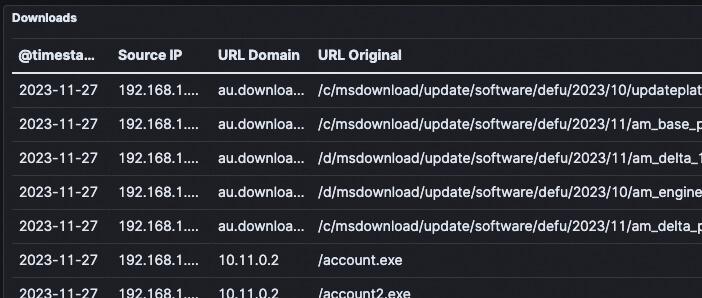
Questionable Downloads
We monitoring file downloads over http across the network to ensure security and compliance.
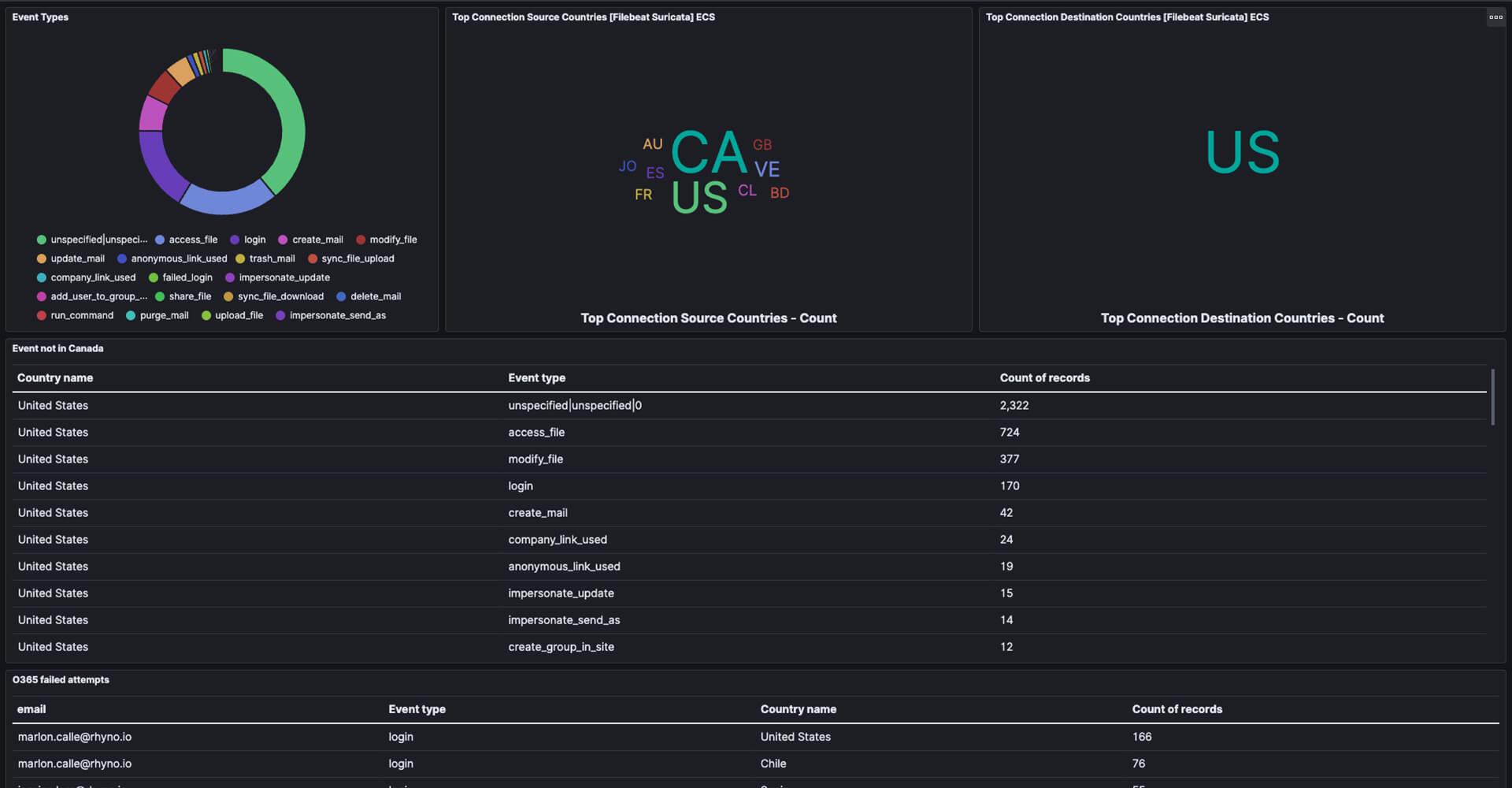
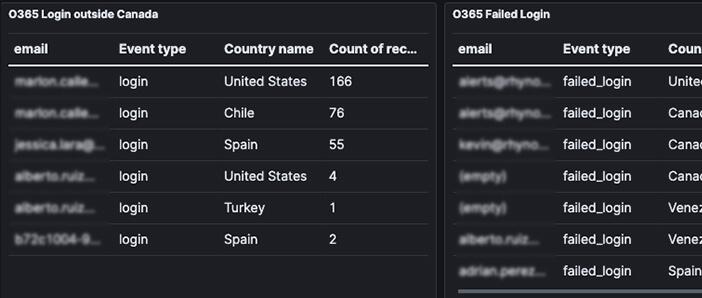
Microsoft 365 Integration
We offer comprehensive surveillance and analysis of authentication activities.
Corporate Privacy Violations
RhynoGUARD's vigilant security monitoring extends to safeguarding corporate privacy.
Data Retention for Compliance
Our approach to data archiving and retention is meticulously designed to meet compliance requirements. We ensure that every piece of transferred network data is securely archived following stringent industry standards and legal mandates.
20-Minute Incident Response SLAs
RhynoGUARD MDR is committed to swift and decisive action in the face of security incidents, backed by our Service Level Agreement (SLA) guaranteeing a 20-minute investigation response time based on incident severity.
Comprehensive and Robust SOC Operations
Our 24/7 monitoring covers your entire IT landscape, ensuring precise identification of genuine threats spanning networks, endpoints, email, cloud, mobile devices, and IoT.
Data Collection
We gather telemetry data from your networks, endpoints, and cloud environments, employing cutting-edge machine learning and behavioral detection engines. This data is subsequently enriched with the latest threat intelligence.Data Analysis
The collected detections are correlated and grouped based on common attributes, resulting in the creation of 'cases.' This approach offers a more comprehensive view of security events.Incident Review
Rhyno's 24/7 Security Operations Centre experts conduct triage on cases, and those requiring attention are prioritized and escalated to your security team as incidents.Incident Response
We provide concise remediation guidance and implement automated response measures to rapidly disrupt, contain, and eliminate threats, preventing damage and disruption.
What Our Customers Say
5/5 - BASED ON 40 REVIEWS
Security Orchestration
Enhanced Threat Awareness and Decision-Making Advantage
Our team of MDR experts seamlessly integrate high-fidelity security telemetry into your technology stack. This data is meticulously assessed against recognized frameworks like MITRE ATT&CK to reduce the risk of visibility gaps. Furthermore, we enhance this telemetry with up-to-the-minute threat intelligence, significantly enhancing real-time detection capabilities against the most current adversarial methods and tactics.
Threat Hunting
Proactively Identifying Both Recognized and Unrecognized Threats in the Initial Phases of an Attack
Utilizing a blend of manual and machine-assisted methodologies, we persistently scour for signs of compromise. This includes fine-tuning security systems to gain deeper insights into routine network behavior, developing watchlists, and executing scenario-driven tests to validate the efficiency of controls and protocols.
Event-Based Response
Promptly Addressing Critical Security Needs
Rhyno's Security Operations Center (SOC) meticulously assesses and prioritizes all incoming security alerts. When a confirmed incident is pinpointed, we deliver actionable guidance for mitigation and effective incident response. Our services include both remote and on-site support, along with 'Events-based Response' featuring automated playbooks designed to contain and counteract a wide range of threats.
RhynoGUARD Platform
Comprehensive Threat Management, Security Analytics, and Reporting
RhynoGUARD serves as the central threat management platform for delivering our Managed Detection and Response (MDR) solution. It seamlessly integrates with all the foundational technologies that are part of the service, facilitating our SOC team in delivering rapid and secure incident analysis, actionable mitigation advice, automated response measures, and transparent service reporting, all through a unified interface.