Do you or your coworkers keep passwords in an Excel sheet, Word document or Notepad?
The fact is that nearly half of businesses store passwords in spreadsheets and other documents, according to a survey conducted by Pulse on behalf of Hitachi ID, a leading cybersecurity software provider specializing in enterprise identity, privileged access, and password management.
As a result, their sensitive data is jeopardized. Here is why.
What is Cleartext?
Cleartext, also known as plaintext, refers to everyday language. For example, anybody with access to a company’s password database, share drive document, or whatever other files the passwords are stored in can read them if they are kept in clear text.
This is convenient but not secure. Passwords and data in these files are also visible to hackers if data is exfiltrated. In cryptography, cleartext refers to communication before encryption.
Take a look at these leaked documents where stolen data is exposed.

When a cleartext communication is encrypted, however, the characters become jumbled and unreadable. The jumbled text is thus referred to as cyphertext. One step further is to “salt” the password by adding extra characters at the beginning or end. Cyphertext is usually combined with an encryption key, which allows the keyholder to decode the jumbled data and restore it to readable form (in other words, decrypt it). When we talk about encrypting passwords, we refer to the entire process as “password hashing.”
If hackers get a hold of hashes, it will be nearly impossible for them to decrypt passwords without the key.
Why, then, do businesses continue to keep passwords in plaintext?
Unfortunately, businesses don’t always take security very seriously. Or they decide to forego security in favour of convenience. In other instances, the company may store your passwords properly; however, they might include logging features that log passwords in plain text regardless.
The good news is that I can show you how to protect yourself and your computer. As a result, you never have to worry about your password being exposed and potentially stolen. Please keep in mind that this is a simple procedure, whereas there are more robust, enterprise-level tools for companies out there.
Easy password hashing (I think!)
Hashing passwords adds an extra degree of protection. Passwords can be saved using hashing in a way that is impossible for hackers to reverse for any realistic amount of time or money.
The cleartext password is converted into a string of characters with a set length using hashing techniques. The hash result won’t resemble the original plaintext word at all, and it will have the same length no matter how long the plaintext password was. Let me give you an example.
STEP 1
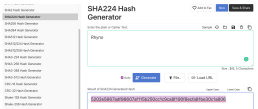
Let’s say I want to remember and store the word “Rhyno,” (needs to be case-sensitive)
I encrypt it with a basic SHA-224 hash generator (you can use other hash generator sites, SHA 224 is SHA 224!). The result will be:
5202e5667adf98607af115b250cc1c9ca8f190f8ecfa81be30c1a806

STEP 2
To create more complexity, let’s add the salt “Cybersecurity” to the beginning of the hash value like this:
Cybersecurity5202e5667adf98607af115b250cc1c9ca8f190f8ecfa81be30c1a806
STEP 3
Now, let’s encrypt this hash with SHAKE-128 to go one step further. The result is:
2fb1fc9ce8e9afb7e5ad8b3769587e292029b2ee535daefb0f447f8a9beb29a7

This result can now be used as a password and won’t be saved anywhere in your files.
Note: if I change one character, the hash will be completely different. Example adding the salt: “cybersecurity” instead of “Cybersecurity” (with small “c”), the result is 71d4ada700b86de80fa46e671e15fc3cd172d405908bd2ab2a8d2d9e70673b3a.
Now I can keep a list of “words” in a document as usual. All I have to do is remember the steps I took and the salt to create the actual password. Heck, I can give it an acronym: SHA-SALT-SHAKE, for example.

Next time I need to retrieve the password, I simply:
- Read my plaintext word: “Rhyno”
- Hash it with SHA-224
- Remember to add “cybersecurity” at the beginning
- Hash the results with SHAKE-128
- Enter the new hash as the password
If you follow these steps correctly, you will get the same results every time. Just make sure to remember the keywords and steps and that it needs to be case-sensitive.
It seems complicated, but it’s easier than you think. You can add the salt (or not). You can also experiment with other combinations. Just make sure you don’t save the resulting hash values on your documents, or it will completely defeat the purpose!
Conclusion
Since the original plain text value contains no information about the resulting hash value, and the salt and steps are in your head only, hackers will never be able to decipher the real password. If your data ever gets stolen and exposed to the world. Heaven forbid! At least the bad guys will never be able to login into your sensitive accounts. Let me know what you think.
Sharing is Caring!
You are welcome to put this blog article on your website, provided you also append an active link to our website “Source: https://rhyno.io/blogs/”
For media enquiries, contact us at [email protected].
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.