A recent version of the Hijack Loader Malware has been seen to use a fresh set of anti-analysis methods to evade detection.
“These improvements try to make the malware more stealthy, so it stays undetected for longer periods of time,” Zscaler ThreatLabz researcher Muhammad Irfan V A stated in a technical paper.
Hijack Loader “now includes modules to add an exclusion for Windows Defender Antivirus, bypass User Account Control (UAC), evade inline API hooking that is often used by security software for detection, and employ process hollowing.”
You might be interested: Cybersecurity guide for small businesses in Canada.
First reported by the cybersecurity firm in September 2023, Hijack Loader, also known as IDAT Loader, is a malware loader. In the interim months, the program has been used to distribute several malware families.
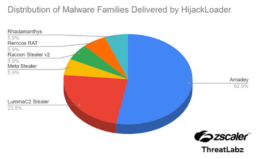
Among these are Amadey, Remcos RAT, Racoon Stealer V2, Meta Stealer, Lumma Stealer (also LummaC2), and Rhadamanthys.
The most recent version distinguishes itself by loading the next-stage payload by decrypting and parsing a PNG image, a method that Morphisec originally described in conjunction with a campaign aimed at Finnish-based Ukrainian companies.
According to Zscaler, the loader has a first stage that extracts and starts the second stage from a PNG image that is either downloaded separately or integrated into it, depending on how the virus is configured.
Irfan clarified, “The primary goal of the second stage is to inject the main instrumentation module. Using several modules, the second stage of the loader uses more anti-analysis measures to boost stealthiness.”
As many as seven new modules are included in hijack loader artifacts found in the wild in March and April 2024. These modules enable the creation of new processes, UAC bypass, and the addition of a Windows Defender Antivirus exclusion via a PowerShell command.
The malware’s use of the Heaven’s Gate method—which CrowdStrike previously revealed in February 2024—to get beyond user mode hooks adds to its invisibility.
“HijackLoader has most often delivered the Madey family,” Irfan remarked. “A PNG picture acquired from the internet or included in the page is used to load the second stage. Furthermore, new modules have been included into HijackLoader to improve its functionality and increase its robustness.”
The development occurs in the context of malware campaigns that use phishing and malvertising to spread various malware loader families, including DarkGate, FakeBat (also known as EugenLoader), and GuLoader.
It also follows the introduction of TesseractStealer, an information stealer supplied by ViperSoftX that extracts text from image files using the open-source Tesseract optical character recognition (OCR) engine.
“The malware concentrates on particular data linked to credentials and cryptocurrency wallet information,” stated Symantec, which is owned by Broadcom. “Aside from TesseractStealer, several of the recent ViperSoftX runs have also been seen to drop another payload from the Quasar RAT malware family.”
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.
