Security experts have recently uncovered a sophisticated “post-exploitation tampering technique” that malicious actors can exploit. This technique allows them to execute covert attacks by visually deceiving iPhone users into thinking their device is in Lockdown Mode, even when it’s not.
[FREE E-BOOK] The Definite Blueprint for Cybersecurity in Manufacturing
This unique method, meticulously outlined by Jamf Threat Labs in a paper shared with The Hacker News, “shows that if a hacker has already infiltrated your device, they can cause Lockdown Mode to be ‘bypassed’ when you trigger its activation.”
In simpler terms, the goal is to enact a Fake Lockdown Mode on a compromised device that has been accessed through alternative means, such as exploiting unpatched security vulnerabilities capable of executing arbitrary code.
Introduced by Apple in the previous year with iOS 16, Lockdown Mode stands as an advanced security feature. Its primary objective is to shield high-risk users from sophisticated digital threats, like mercenary spyware, by minimizing the potential attack surface. This strategic measure aims to fortify the defence against targeted and intricate cyber attacks.
However, it does not outright prevent the deployment of malicious payloads on a compromised device. This vulnerability opens the door for a trojan, already planted on the device, to exploit Lockdown Mode, misleading consumers into believing they are secure.
“In the case of an infected phone, there are no safeguards in place to stop the malware from running in the background, regardless of whether the user activates Lockdown Mode or not,” stated security researchers Hu Ke and Nir Avraham. “Both of these safeguards are in place.”
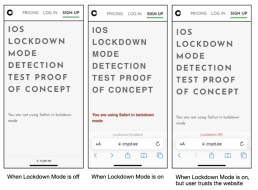
The fake Lockdown Mode is accomplished by hooking functions – e.g., setLockdownModeGloballyEnabled, lockdownModeEnabled, and isLockdownModeEnabledForSafari – that are triggered upon activating the setting so as to create a file called “/fakelockdownmode_on” and initiate a userspace reboot, which terminates all processes and restarts the system without touching the kernel.
This also means that a piece of malware that has been put on the device without any kind of persistence mechanism will continue to exist even after a reboot of this kind and will covertly spy on the people who use it.
To add insult to injury, an enemy may change the Lockdown Mode on the Safari web browser in order to make it possible to view PDF files, which are normally restricted while the mode is activated.
“Since iOS 17, Apple has elevated Lockdown Mode to kernel level,” the researchers were quoted as saying. “This strategic move is a great step in enhancing security, as changes made by Lockdown Mode in the kernel typically cannot be undone without undergoing a system reboot, thanks to existing security mitigations.”
Jamf’s revelation comes approximately four months following the disclosure of yet another inventive method within iOS 16. This approach, if exploited, allows for sustained access to an Apple device while evading detection. The technique involves duping the victim into thinking their iPhone is in airplane mode.
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.
