In an ongoing supply chain attack, a digitally signed and trojanized version of the 3CX Voice Over Internet Protocol (VOIP) desktop client is reportedly being used to target the company’s customers.
3CX is a VoIP IPBX software development company with over 600,000 companies worldwide and over 12 million daily users using its 3CX Phone System.
Customers include high-profile companies and organizations such as American Express, Coca-Cola, McDonald’s, BMW, Honda, Air France, Toyota, Mercedes-Benz, IKEA, and the United Kingdom’s National Health Service (who published an alert on Thursday).
According to Sophos and CrowdStrike security researchers, the attackers are targeting both Windows and macOS users of the compromised 3CX softphone app.
“The malicious activity includes beaconing to actor-controlled infrastructure, deployment of second-stage payloads, and, in a few cases, hands-on-keyboard activity,” CrowdStrike’s threat intelligence team explained.
“The spawning of an interactive command shell has been observed to be the most common post-exploitation activity observed to date,” Sophos added in an advisory distributed through its Managed Detection and Response service.
While CrowdStrike believes this attack was carried out by a North Korean state-backed hacking group known as Labyrinth Collima, Sophos researchers say they “cannot verify this attribution with high confidence.”
Labyrinth Collima activity is known to overlap with that of other threat actors such as Kaspersky’s Lazarus Group, Dragos’ Covellite, Mandiant’s UNC4034, Microsoft’s Zinc, and Secureworks’ Nickel Academy.
“When it comes to adversary naming conventions, CrowdStrike has an in-depth analytic process,” the company told BleepingComputerr via email.
“LABYRINTH CHOLLIMA is a subset of what has been described as Lazarus Group, which includes other DPRK-nexus adversaries, including SILENT CHOLLIMA and STARDUST CHOLLIMA.”
Supply chain attack on SmoothOperator software
In reports published Thursday evening, SentinelOne and Sophos also revealed that the trojanized 3CX desktop app is being downloaded in a supply chain attack.
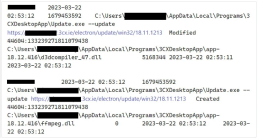
SentinelOne has dubbed this supply chain attack ‘SmoothOperator,’ and it begins when the MSI installer is downloaded from 3CX’s website or an update is pushed to an already installed desktop application.
When the MSI or update is installed, malicious ffmpeg.dll [VirusTotal] and d3dcompiler 47.dll [VirusTotal] DLL files are extracted and used to carry out the next stage of the attack.
While Sophos claims that the 3CXDesktopApp.exe executable is not malicious, it will be sideloaded and used to extract and decrypt an encrypted payload from d3dcompiler 47.dll.
This decrypted d3dcompiler 47.dll shellcode will be executed to download icon files hosted on GitHub that contain Base64 encoded strings appended to the end of the images, as shown below.
According to the GitHub repository where these icons are stored, the first icon was uploaded on December 7th, 2022.
According to SentinelOne, the malware uses these Base64 strings to download a final payload, a previously unknown information-stealing malware downloaded as a DLL, to the compromised devices.
This new malware can harvest system information as well as steal data and stored credentials from Chrome, Edge, Brave, and Firefox user profiles.
“We cannot confirm that the Mac installer is similarly trojanized at this time. Our ongoing investigation includes other applications, such as the Chrome extension, which could be used to stage attacks “According to SentinelOne.
“The threat actor has registered a sprawling set of infrastructure as early as February 2022, but there are no obvious connections to existing threat clusters at this time.”
3CX confirms that software has been compromised.
3CX CEO Nick Galea confirmed in a forum post Thursday morning that the 3CX Desktop application had been compromised and contained malware. As a result, Galea recommends that all customers uninstall the desktop app and instead use the PWA client.
“As many of you have noticed, the 3CX DesktopApp contains malware. It has an impact on the Windows Electron client for customers who are running update 7. It was reported to us last night, and we are currently working on an update to the DesktopApp that will be released in the coming hours “Galea mentioned it in the 3CX forums.
“We’re still investigating the situation in order to provide a more detailed response later today. Here’s a rundown of what we’ve accomplished thus far.”
3CX has yet to specify which library they are referring to or whether it was the cause of their developer environment being compromised.
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.