According to a Gurucul study, insider threats are the top concern for all types of organizations, with only 3% of survey respondents saying they are not concerned about insider risk.
With answers from over 325 cybersecurity professionals, the report looks at the latest trends and challenges organizations face as they try to adapt to changing insider threats. It also looks at how organizations are getting ready to protect critical data and IT infrastructure better.
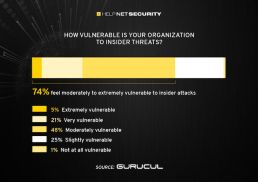
The report found that organizations have never felt more vulnerable, with three-quarters of respondents saying they feel moderate to extremely vulnerable to insider threats. This is an increase of 8% over the previous year.
This rise in perceived vulnerability is happening simultaneously with a big surge in insider attacks. 74% of organizations say that attacks are happening more often, which is a 6% increase from last year. In addition, 60% of organizations have had at least one attack, and 25% have had more than six.
Organizations also have trouble with insider threats in the cloud and don’t always have the right technical tools to find and stop them.
87% of organizations think having unified visibility and control across all apps, devices, web destinations, on-premises resources, and infrastructure is essential.
But only 48% keep an eye out for strange behaviour on the web and in the cloud. Also, more than half of the people who answered said that it is harder to find insider threats in the cloud and that the uptime and performance of tools like SASE and CASB are crucial to success.
This report shines a light on some of the most interesting insider threat problems organizations are facing right now. Even though it shows that 86% are using some kind of solution to track user behaviour, it was surprising to see that access logging was the most common method and that only 25% are using automated tools to track user behaviour 24 hours a day, 7 days a week, comments Saryu Nayyar, the CEO of Gurucul.
There are many different types of monitoring and analytics that organizations use to find insider threats. “This shows how important it is to have better tools and processes to analyze data behaviour, user behaviour, access and movement across a network, both internally and externally, to find and stop insider attacks,” he explains.
Some other key facts from the report include:
Trusted insiders who already have credentials to access apps, networks, and services (54%), more people using SaaS apps that can leak data (44%), and more people using personal devices that can access corporate resources (42%) are the top things that make it hard to find and stop insider attacks quickly.
60% of cyber security professionals are most worried about IT users and admins who have access to a lot of information. Then come third-party contractors and service providers (57%), regular employees (55%), and privileged business users (53%).
The rising risk of insider attacks is a strong reason for companies to set up formal programmes to deal with insider risk. 39% of companies already have a programme to deal with threats from inside the company. Another 46% want to add insider threat programmes in the future. This is a 5% increase from the year before.
Moving to hybrid work and working from home has worsened insider risk. 68% of security professionals are worried or very worried about insider risk when they think about going back to work after COVID or switching to a permanent hybrid work model.
At 77%, compromised accounts or machines are the most worrying type of attack. However, accidental and careless data breaches were more worrying than malicious data breaches. It’s a good reminder that user mistakes and accidental policy breaks can be just as bad as intentional ones.
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.