The process of proactively searching for cyber threats that are hiding undiscovered in a network is known as threat hunting. Cyber threat hunting scans your environment for dangerous actors who bypassed your first endpoint security measures.
An attacker can remain on a network for months after slipping in, silently collecting data, looking for confidential material, or obtaining login credentials that will allow them to move laterally throughout the environment.
When an attacker manages to evade detection and an attack penetrates an organization’s defences, many organizations lack the advanced detection capabilities needed to prevent advanced, persistent threats from remaining on the network. Therefore, threat hunting is a critical component of any security plan.
Methodologies for Threat Hunting
Threat hunters presume that enemies are already present in the system and begin investigating odd behaviour that may signal the presence of hostile activities. This first inquiry in proactive threat hunting often falls into three major categories:
1. Hypothesis-driven research
Hypothesis-driven investigations are frequently initiated by a new threat discovered in a vast pool of crowdsourced attack data, providing insights into attackers’ most recent strategies, approaches, and processes (TTP). Once a new TTP has been uncovered, threat hunters will investigate whether the attacker’s unique actions may be seen in their own environment.
2. Investigation based on known Compromise Indicators or Attack Indicators
Using tactical threat intelligence, this strategy to threat hunting catalogs known IOCs and IOAs linked with new threats. Threat hunters then use these as triggers to identify possible covert assaults or continuing malicious activities.
3. Research into advanced analytics and machine learning
The third option uses advanced data analysis and machine learning to filter through huge amounts of data in order to spot abnormalities that might indicate hostile activity. These abnormalities become hunting leads, which are followed up on by expert analysts in order to discover uncovered threats.
All three techniques include a human-powered effort to defend an organization’s systems and information by combining threat intelligence resources with modern security technologies.
See Rhyno Cybersecurity in Action!
Threat Hunting Procedures
Proactive cyber threat hunting often consists of three steps: a trigger, an investigation, and a resolution.
The Trigger is the first step.
When sophisticated detection systems notice odd activities that may suggest a malicious activity, a trigger directs threat hunters to a specific system or region of the network for additional study. A notion about a new threat is frequently the catalyst for proactive hunting. A security team, for example, may look for sophisticated threats that employ techniques like file-less malware to circumvent existing safeguards.
Step 2: Conduct an investigation
During the investigation phase, the threat hunter uses technologies like EDR (Endpoint Detection and Response) to examine a system’s possible hostile intrusion thoroughly. The inquiry will continue until either the activity is deemed benign or a comprehensive picture of the harmful behaviour is developed.
Step 3: Make a decision.
During the resolution phase, pertinent malicious activity intelligence is communicated to operations and security teams so that they may respond to the event and minimize dangers. Without further human interaction, the data obtained concerning both harmful and benign activities may be fed into automated systems to increase its efficacy.
Throughout the process, cyber threat hunters acquire as much information about an attacker’s actions, techniques, and intentions as possible. They also evaluate acquired data to identify patterns in an organization’s security environment, eradicate present weaknesses, and forecast future security.
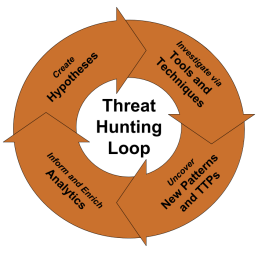
What Role Does Threat Hunting Play?
Threat hunting is a valuable addition to the conventional incident detection, response, and remediation procedure. While security systems scan raw data to create alarms, threat hunting uses queries and automation to derive hunting leads from the same data.
Human threat hunters who are adept in spotting signals of enemy activity then examine hunting leads, which may subsequently be handled through the same pipeline.
Should You Hire a Threat Hunting Service?
Although the notion of threat hunting is simple, the issue is finding employees who can carry out the activity correctly. The finest threat hunters are battle-tested veterans with extensive experience confronting cyber enemies.
Unfortunately, there is a significant skills shortage in the cybersecurity field when it comes to threat hunting, which means that experienced hunters are not cheap. That is why many firms are turning to managed services, which can provide deep knowledge and 24×7 surveillance at a lower cost.
Let’s look at what to look for in a threat-hunting service below:
What Do You Need to Begin Threat Hunting?
A leading threat-hunting service approaches attacks in three ways. In addition to trained security personnel, it includes two additional components that are necessary for effective hunting: huge data and advanced analytics.
1. Human Resources
Every new generation of security technology can identify a greater number of complex dangers, but the human brain remains the most effective detection engine. Furthermore, automated detection approaches are inherently predictable, and today’s attackers are well aware of this and have devised methods to circumvent, avoid, or conceal from automated security systems. Therefore, human threat hunters are an essential component of a successful threat-hunting service.
Because proactive hunting requires human engagement and intervention, success is determined by who searches through the data. Intrusion analysts must have the expertise to detect complex targeted assaults, as well as the security resources to respond to any unexpected activity.
2. An Abundance of Data
In order to give complete visibility into all endpoints and network assets, the service must also be able to collect and store granular system event data. An intelligent security service then collects and performs real-time analysis on these big data volumes using scalable cloud infrastructure.
3. Intelligence on Threats
Finally, a threat-hunting solution should be capable of cross-referencing internal organizational data with the most recent threat information concerning external trends, as well as employing advanced technologies to evaluate and correlate harmful behaviours properly.
All of this takes time, resources, and attention — and most companies aren’t appropriately staffed or prepared to operate a continuous, round-the-clock threat-hunting operation. Fortunately, managed security solutions provide the essential resources — people, data, and analytical tools — to seek abnormal network activity and hidden dangers successfully.
MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.