Zaraza bot is a recently discovered malware that is designed to steal user credentials and is actively being sold on Telegram, a popular messaging app that is widely used by cybercriminals for communication and coordination. To make matters worse, the attackers behind the Zaraza bot are using Telegram as a command-and-control server.
“Zaraza bot targets a large number of web browsers and is being actively distributed on a Russian Telegram hacker channel popular with threat actors,” cyber security firm Uptycs stated in a research published last week.
“Once the malware infects a victim’s computer, it retrieves sensitive data and sends it to a Telegram server, where the attackers can access it immediately.”
Zaraza bot, a 64-bit binary file in C#, has the ability to target a wide range of web browsers, including popular ones like Google Chrome, Microsoft Edge, Opera, AVG Browser, Brave, Vivaldi, and Yandex, totalling up to 38 different browsers. Additionally, the malware can take screenshots of the currently active window, which can provide the attackers with sensitive information about the victim’s activities.
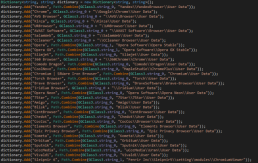
This credential-stealing malware is the latest threat to valuable online services, such as online bank accounts, bitcoin wallets, email accounts, and other websites.
The theft of credentials is a significant concern as it allows threat actors to gain unauthorized access to victims’ accounts and potentially engage in identity theft and financial fraud. With stolen login information, attackers can pose as the victim and gain access to sensitive personal and financial data.
Uptycs has obtained evidence that the Zaraza bot is being offered as a commercial tool for other hackers in exchange for a subscription. Currently, it is unclear how the malware spreads, but in the past, information thieves have used various methods, such as malvertising and social engineering.
It is important to note that malware-as-a-service (MaaS) is becoming more prevalent among cybercriminals, and it can allow even inexperienced attackers to carry out sophisticated attacks. Therefore, it is crucial for users to remain vigilant and take necessary precautions to protect themselves from such threats.

MANAGED CYBERSECURITY SOLUTIONS
Rhyno delivers a range of activities that combine to fully protect your infrastructure and data from cybercriminals, anywhere and everywhere, 24/7/365.
About Rhyno Cybersecurity Services
Rhyno Cybersecurity is a Canadian-based company focusing on 24/7 Managed Detection and Response, Penetration Testing, Enterprise Cloud, and Cybersecurity Solutions for small and midsize businesses.
Our products and services are robust, innovative, and cost-effective. Underpinned by our 24x7x365 Security Operations Centre (SOC), our experts ensure you have access to cybersecurity expertise when you need it the most.