Build A Culture Of Trust & Security
Fully-managed cybersecurity awareness training with real-time social engineering simulations.
Employees are the last line of defense
We deliver personalized awareness training and attack simulation programs based on your unique cybersecurity needs.
Benchmarking
We provide baseline testing to assess the phish-prone percentage of your users through a simulated attack.
Spear phishing simulations
SMS & portable media attacks
File attacks (PDF, Java, Macro, etc.)
Website cloner
Training
We create and perform a personalized cybersecurity awareness training program based on your specific security needs.
Interactive training content
Customizable e-learning movies
Role and Reputation-based training
Integrated LMS with Android & iOS apps
Simulation
We deliver best-in-class, simulated attacks using proven techniques and hundreds of realistic email and landing page templates.
Exposure to phishing & malware
Detection of browser vulnerabilities
Spoofing & Ransomware simulation
Mail and Web filter tests
Report & Retrain
Our enterprise-strength reporting delivers stats for both security awareness training and phishing, ready for management.
Cybersecurity Risk Scoring
Advanced Reporting Features
Security awareness training stats
Security Compliance Reporting
Put a checkmark on your annual or compliance security awareness training
Get ready for SOC 2 and ISO 27001 audit or just stay compliant with data privacy laws and regulations. Quick and easy setup. No annual commitment.
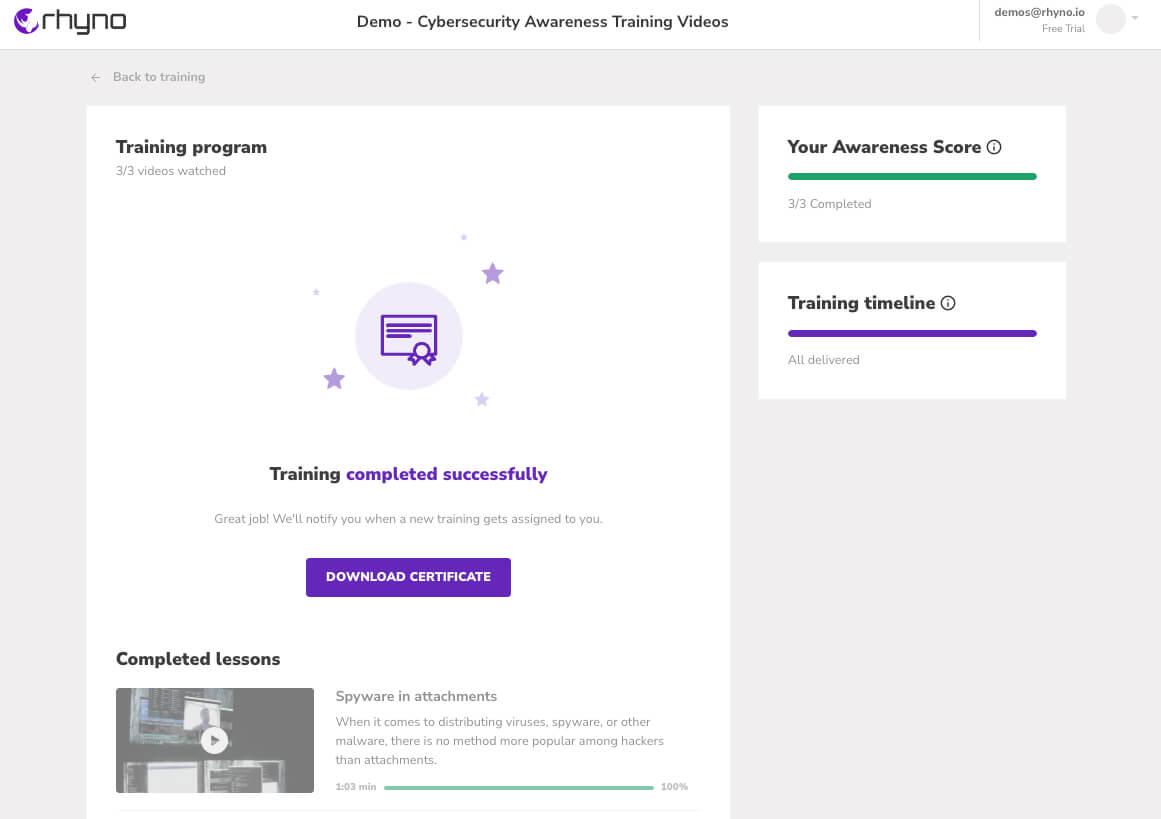
Interactive scenarios that go wider and deeper than company questionnaires and don’t set employees up to fail
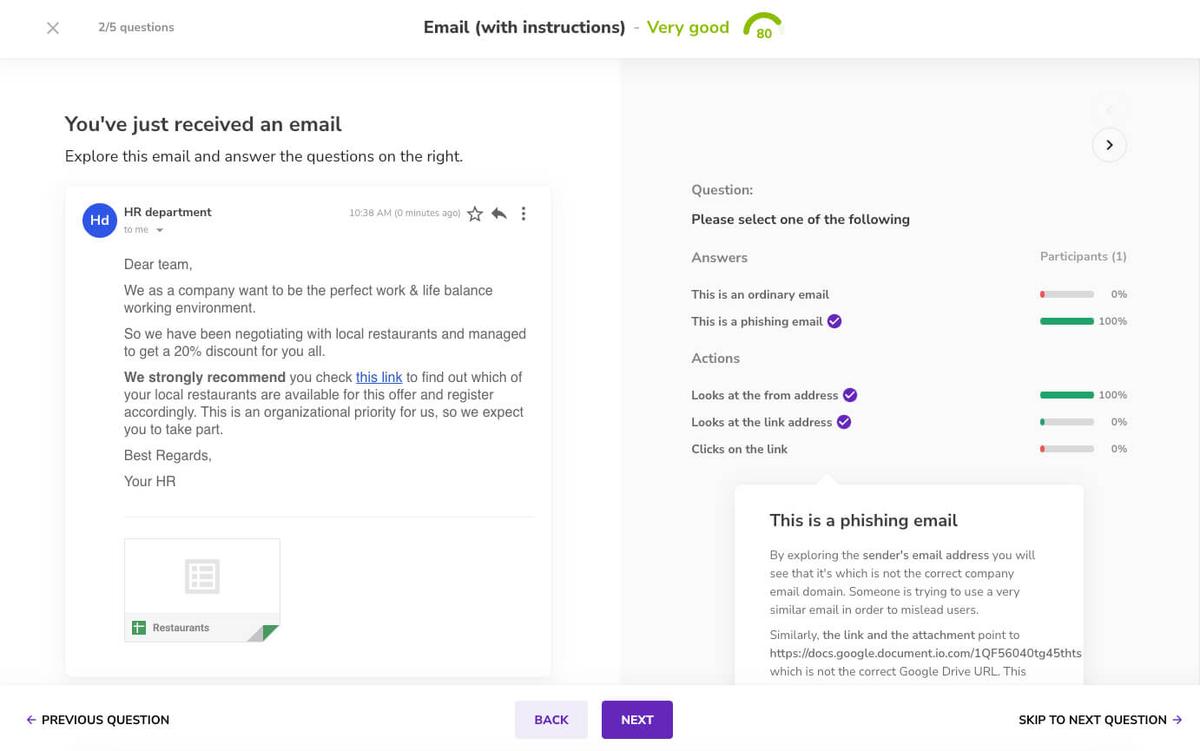
Test your employees just like hackers would — use your company and employee data to make simulations realistic
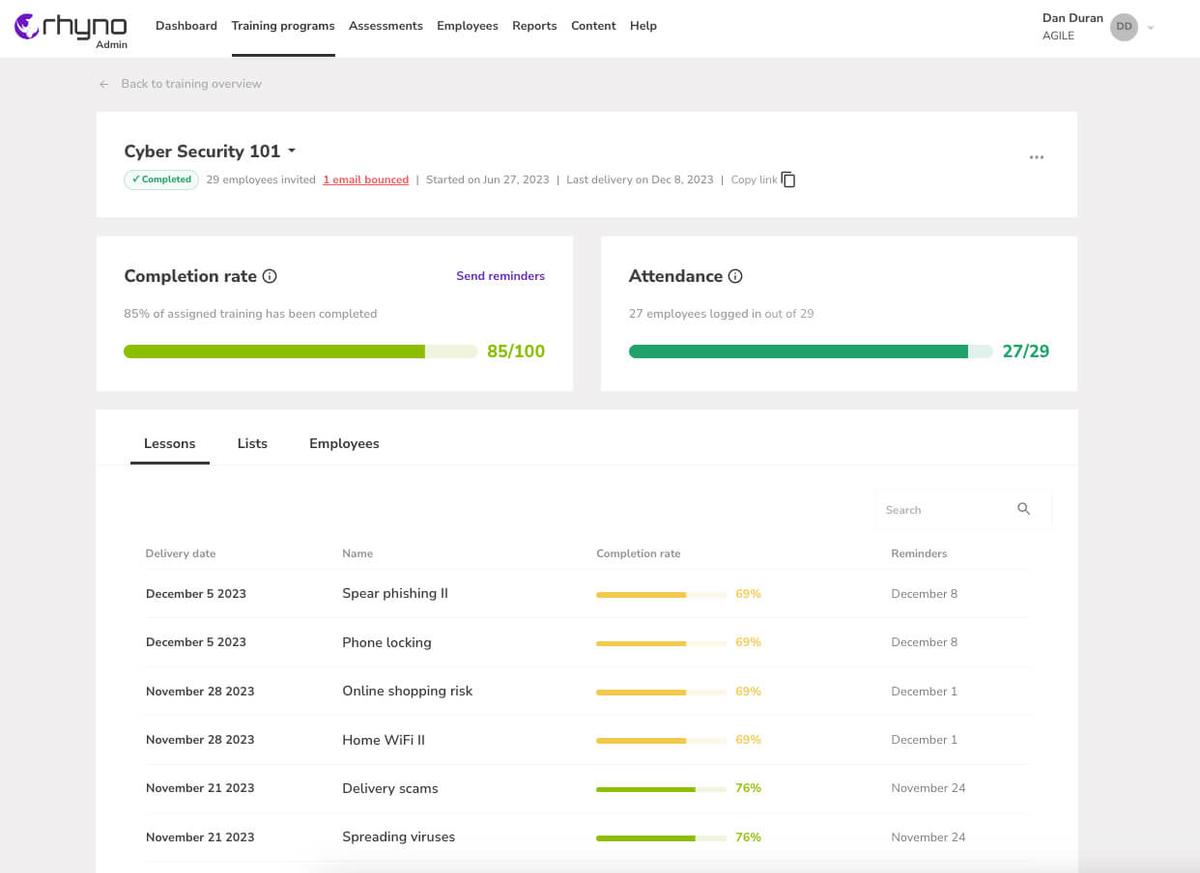
Seize employee attention to prompt desired cyber behavior or teach ways of identifying cyber threats
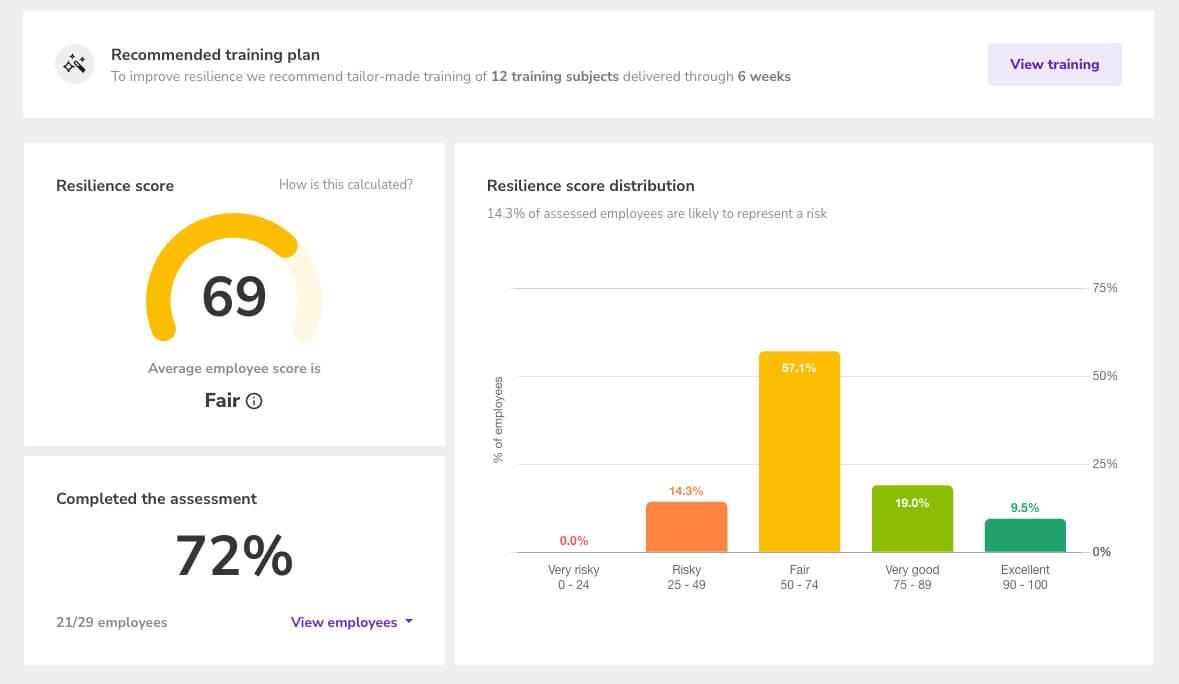
Schedule lessons over weeks, send notifications and reminders via mail, Slack or Teams, and track progress
Deliver training in bite-sized chunks spaced over weeks. Increase both retention and reduce the load on learners
Deliver focused training your employees need, not same-for-all generic training
Integrate with Active Directory, Google Workspace or your own SSO system. Enable Slack or Teams training bots
Security awareness training is available in 18+ languages and works with any existing learning management system
Our videos are localized with voice-overs in 18+ languages, and accessible with captions
If you already have an existing delivery solution in place, easily integrate our content with code snippets or the SCORM standard
We release new materials monthly to cover emerging cyber threats
100+ original pieces of content — from curated training programs to digital nudges and everything in between
No cartoons! Because your employees are grownup professionals who don’t need superheroes
Use these cyber awareness assets in your internal communication to keep cybersecurity top-of-mind
160 cybersecurity leaders in our panel share their opinions, techniques and experiences with us. Learn from them
Curated and paced programs created by cybersecurity and behavioral experts to keep employees engaged
Start immediately with programs created by our security and behavior experts — or create custom programs
Perks
Dashboard
Monitor training programs, attendance, and score
Insights
Identify and focus on vulnerable departments and individuals
20+ training programs
Curated lesson bundles that address specific threat areas
Scheduled delivery and reminders
Spaced delivery over weeks increases retention
Certificates
Employees win certificates for successful training
Employee management
Manage departments, integrate with Active Directory, Google Workspace, or your SSO solution
AwareGO is SOC 2 Compliant
We have the governance, systems, and infrastructure in place to protect client information from unauthorized access.
Works with existing solutions
Our platform is built to integrate with phishing simulation, attack surface management, SIEM, MSSP and LMS platforms
White label
Make the platform your own with a custom logo and colors
Works across devices
Built from the ground up for cross-device support
In your language
Available in 18 languages with more being added
Flexible pricing
Our pricing is based on the number of employees in your organization, and the products and services you want to use.
How to get started
Explore how to deploy targeted training and discover our relatable, retainable and fun cybersecurity awareness videos
You and your employees are going to love AwareGO. It’s a modern, cloud-based system for managing human risk, from assessment to remediation. We’ve made it super easy — schedule your first assessment or training in minutes.
Get started for free and give it a go right now.
You’ll love the way AwareGO can fit into your existing infrastructure. Our robust APIs, widgets, and content available in SCORM format make sure that the integration is seamless. We also integrate with Active Directory, Google Workspace, and popular tools like Slack and Teams.
Contact us and our experts will recommend the best way to integrate.
Upgrade your cybersecurity business by adding human risk management to your existing portfolio of services. Increase your deal size by leveraging Human Risk Assessment or offering Security Awareness Training to your current customers and creating a new revenue stream.
Contact us to become an AwareGO partner, and we will support you every step of the way.
What Our Customers Say
5/5 - BASED ON 40 REVIEWS